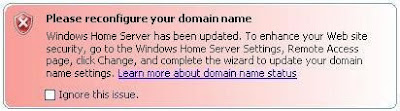
How to turn on back Windows Live domain?
- To reconfigure your domain name, open your Windows Home Server Console and click the Settings button.
- Once the Settings are open, click the Remote Access.
- As you can see, the Domain Name Status still informs you that it is working. Your Remote Access page should still be viewable away from your home. However, a trusted SSL certificate has not been setup as the earlier Network Health notification informed you.
- To complete the setup, click the Unconfigure button. After clicking the Unconfigure button, it will change to a Setup button. Click the Setup button to install a trusted SSL certificate for your HomeServer.com domain name.
- Once the Setup button has been clicked, the Domain Name Setup Wizard will open. Click the Next button to continue.
- The Domain Name wizard will ask you to verify your Windows Live ID that you previously used to setup your personalized HomeServer.com Domain. Type in your Windows Live E-mail Address and Password and click Next.
- The Domain Name wizard will display all registered names linked to your Windows Live account that you just entered. Select the correct domain name and click Next.
- Click Done.
Your Domain Name Status should display Working if you have followed these steps.